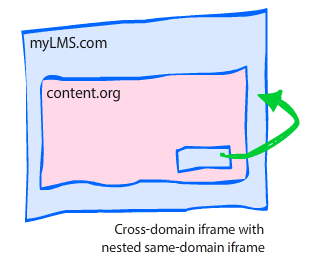
Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign - Microsoft Security Blog

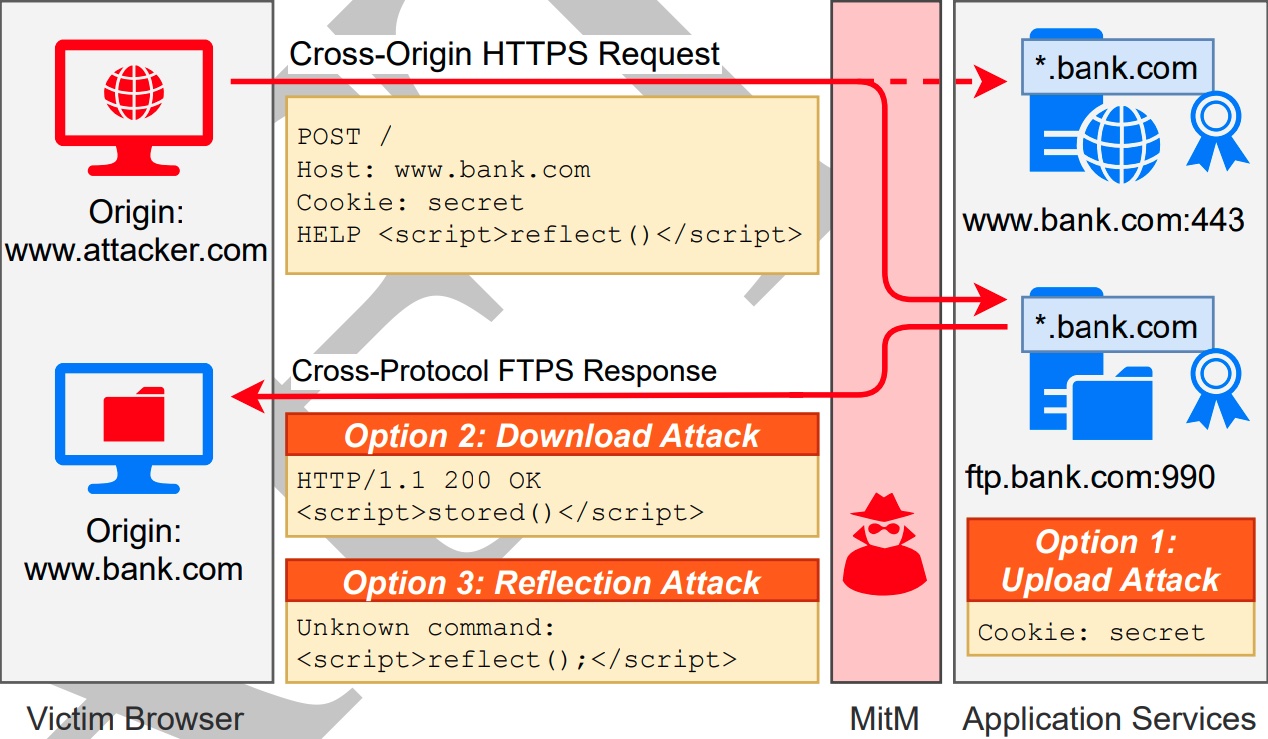
Cross-origin resource sharing (CORS) Explanation & Exploitation ☠ | by Hashar Mujahid | InfoSec Write-ups