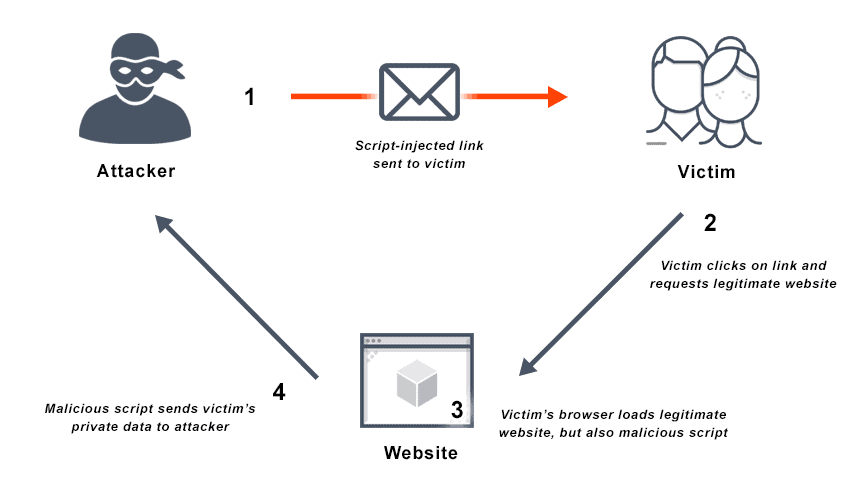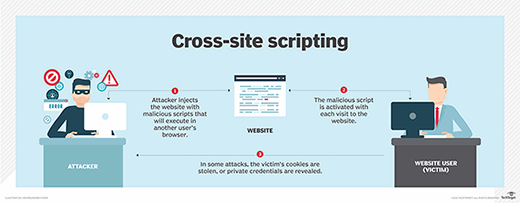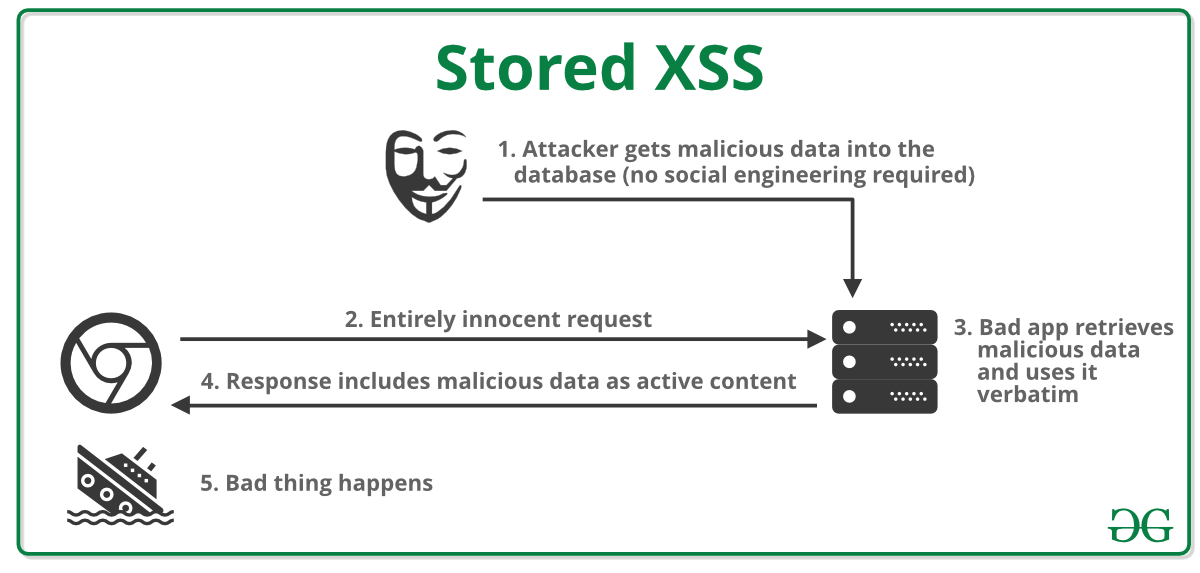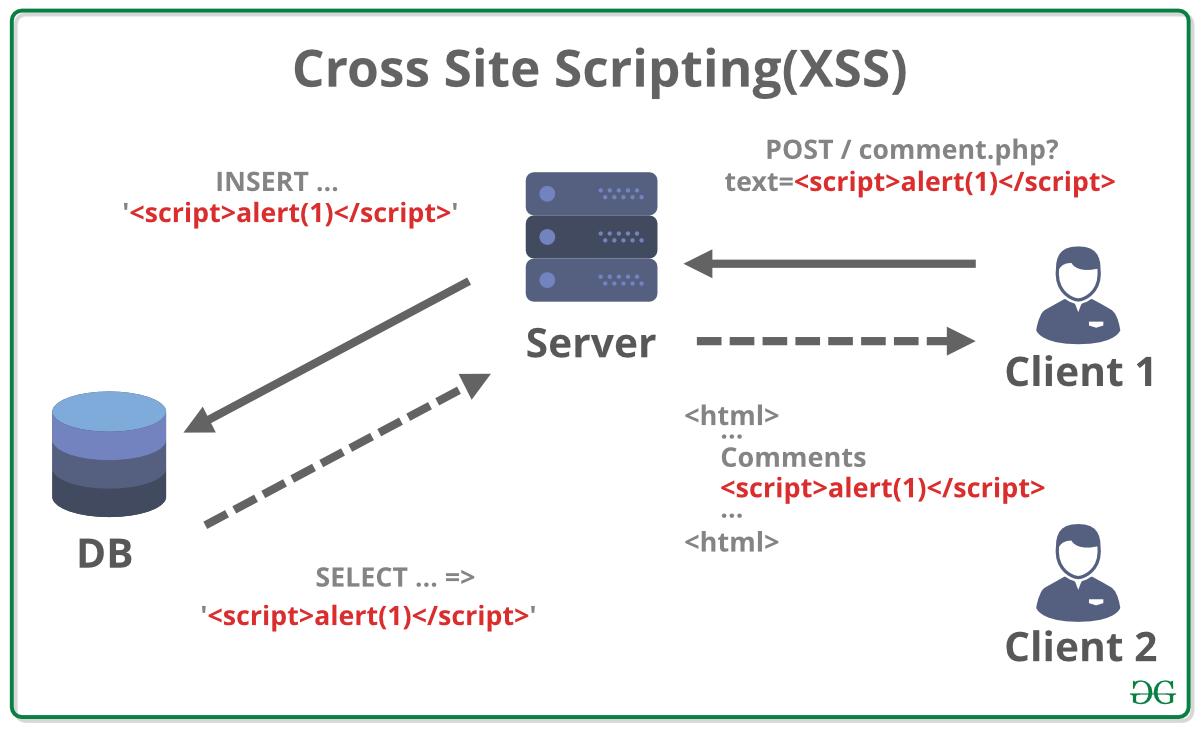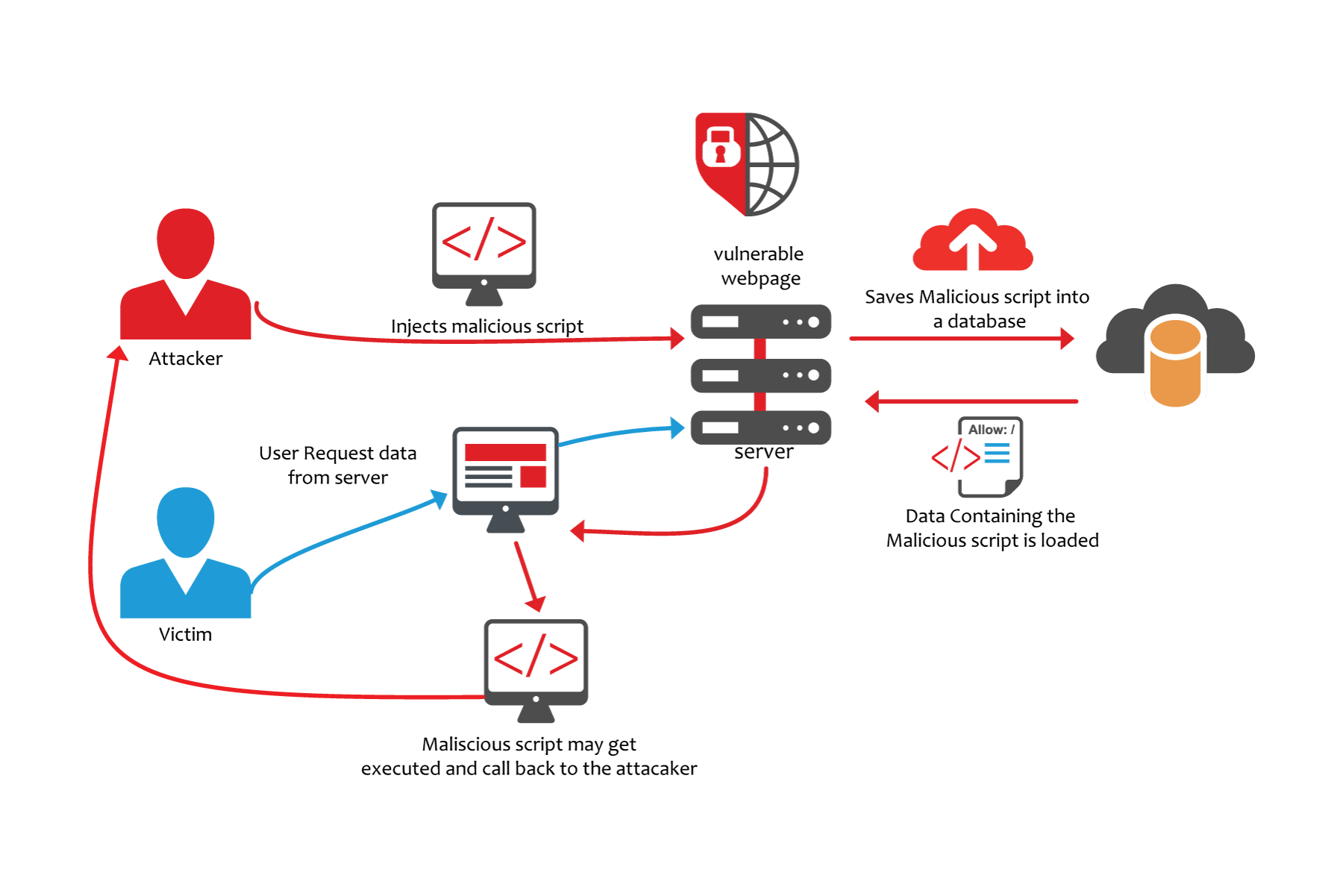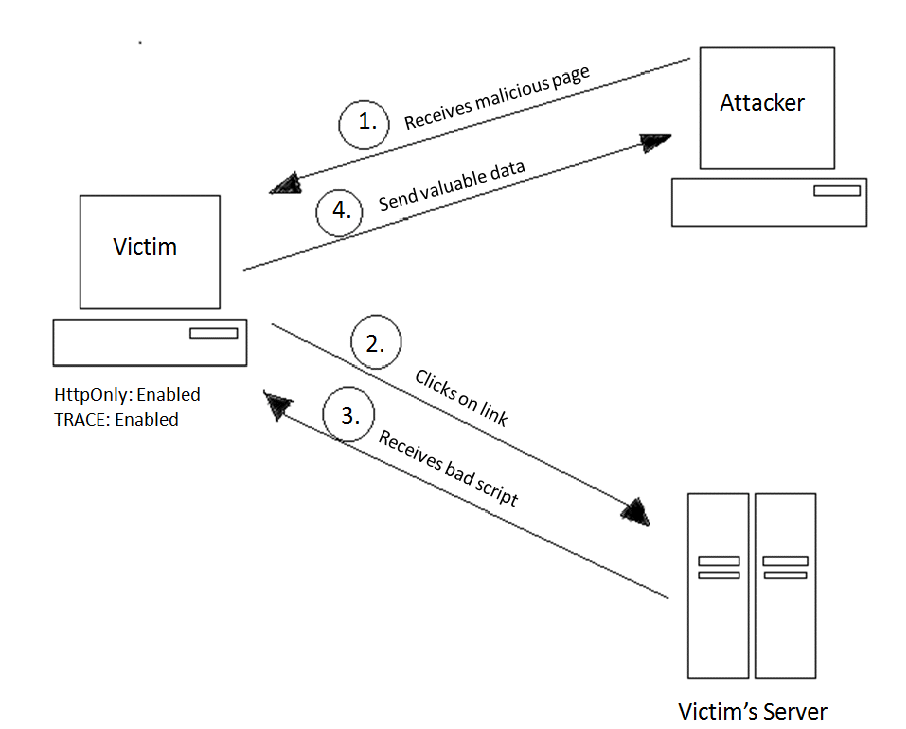
Securing Apache, Part 4: Cross-site Tracing (XST) & Cross-site History Manipulation (XSHM) - Open Source For You
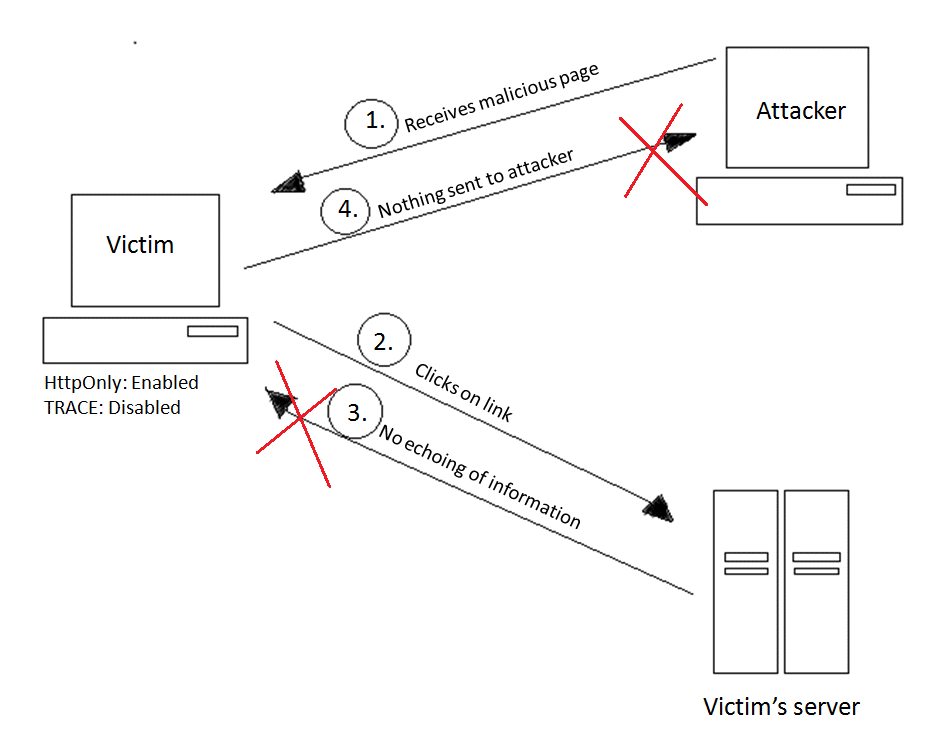
Securing Apache, Part 4: Cross-site Tracing (XST) & Cross-site History Manipulation (XSHM) - Open Source For You

Non-Hermitian physics for optical manipulation uncovers inherent instability of large clusters | Nature Communications

Embedded Microbubbles for Acoustic Manipulation of Single Cells and Microfluidic Applications | Analytical Chemistry
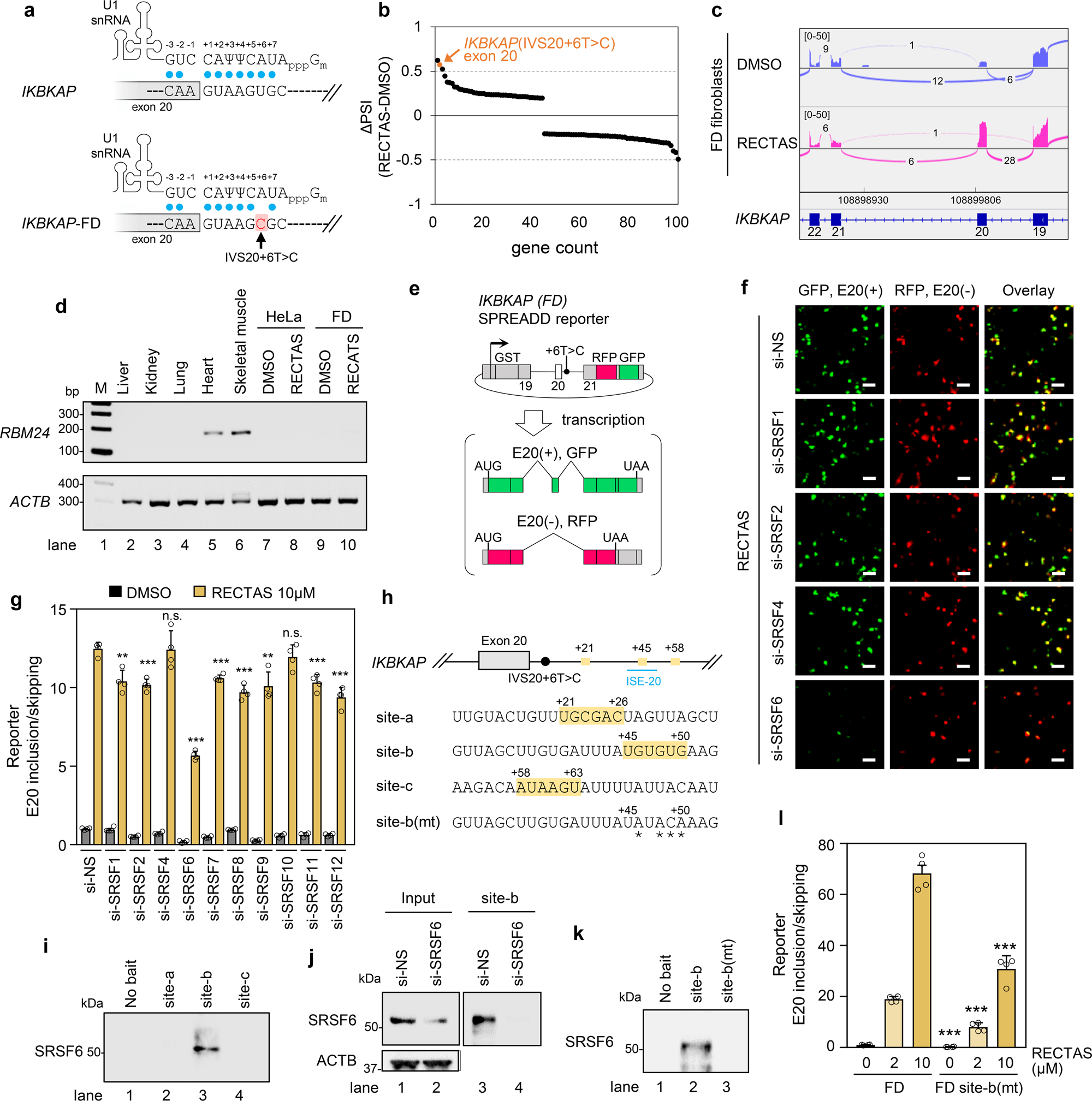
Therapeutic manipulation of IKBKAP mis-splicing with a small molecule to cure familial dysautonomia | Nature Communications

Cross Site History Manipulationの仕組みや具体的な攻撃手法がいまいち分かりません。 この攻撃はあくまでも被害者のブラウザの history.lengthから、その被害者がアクセスしたサイトのレスポンス状況を推測するだけ(=危険性は低い)でしょうか? - ockeghem page
![Kishan Kumar - Web Security Topics for selfstudy [+] Cache Poisoning [+] Cash Overflow [+] Clickjacking [+] Command injection attacks [+] Comment Injection Attack [+] Content Security Policy [+] Content Spoofing [+] Kishan Kumar - Web Security Topics for selfstudy [+] Cache Poisoning [+] Cash Overflow [+] Clickjacking [+] Command injection attacks [+] Comment Injection Attack [+] Content Security Policy [+] Content Spoofing [+]](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=2549411185163312)